
Introduction:
In July this year, the failure of cyber security service provider CrowdStrike caused a "global downtime", and some US airlines, banks, and supermarkets were paralyzed. On that day, CrowdStrike's stock price plummeted, and multiple cyber security and SaaS stocks were also affected.
The incident caused CrowdStrike's stock price to plummet by nearly 50% in two months. Since then, its business has been affected, and many customers have sought discounts when renewing contracts to cover the cost of business interruptions.
But soon, CrowdStrike and NVIDIA announced a collaboration to jointly develop more advanced cyber security solutions, develop customized cyber security solutions, and strengthen cooperation in the fields of cloud security, mobile security, and IoT security. As a result, CrowdStrike's stock price rebounded rapidly, rising nearly 90% from its low point in five months.
In fact, as one of the most important but also overlooked industries in the world, cyber security is the insurance of the technological world. The business of all internet companies may be threatened by security, so top security solutions and companies often have strong bargaining power.
As the focus of AI development shifts from chips and infrastructure to the software layer, cyber security is also becoming a key battlefield. According to relevant analysis, the compound annual growth rate of the global cyber security industry in the next few years will reach 14%, and it will be worth $563 billion by 2032.
CrowdStrike CEO George Kurtz once explained the relationship between cyber security and the AI industry as follows: 'We provide AI capabilities for the security industry and security protection for AI development.'
The following figure shows the Value Chain of the cyber security industry. In this article, the RockFlow research team will delve into the important branches, development, and investment value of related leading companies in the cyber security industry.
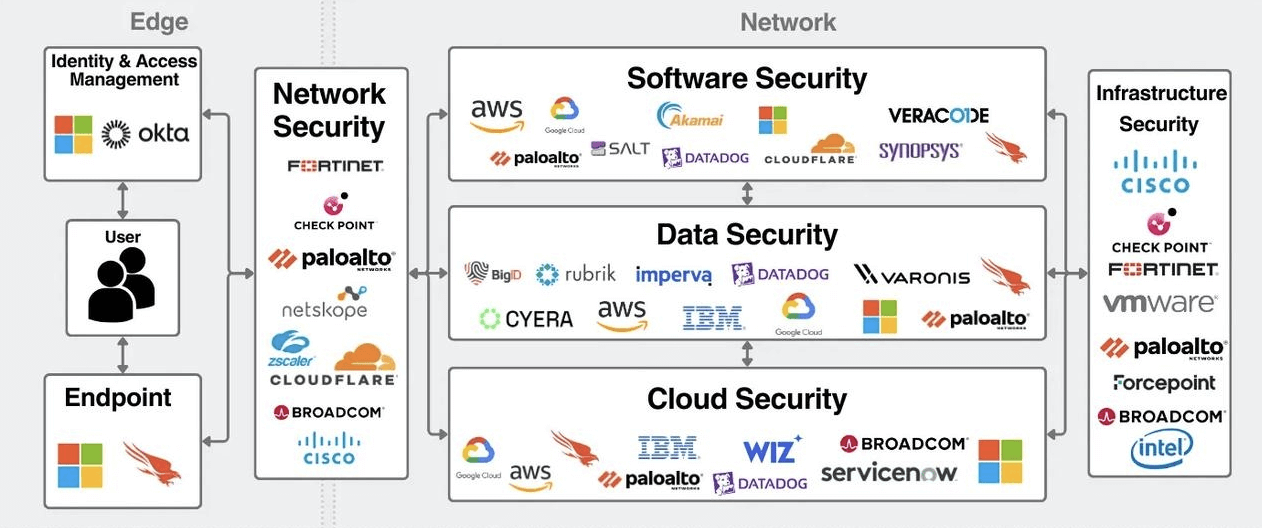
1. Important branches of the cyber security industry
The term "cyber security" covers many scenarios. The current industry consensus believes that important scenarios include Edge Security, Cyber Security, Software Security, Data Security, Cloud Security, etc. The RockFlow research team will elaborate on them one by one below.
Edge security - protecting users and their platforms
The "edge" here refers to the decentralized and decentralized enterprise infrastructure, including users, the devices they use, and the technology that determines whether/how users access the network. Identity and access management (IAM) and endpoint security are the two main parts of the edge category.
Cyber security - protecting data exchange in "trusted" networks
Traditionally, cyber security is a Competitive Edge architecture - blocking threats outside the network to avoid risk events. However, as technology becomes increasingly complex and decentralized, cyber security has also been expanded. The "network" in cyber security refers to the enterprise's network of connected devices, including data centers, cloud environments, applications, etc.
Operational Safety - Lifecycle Technology
This refers to the processes that run through the entire security lifecycle, including process tools aimed at preventing, detecting, or responding to security incidents. These technologies mainly include managed services, monitoring, governance, security information and event management (SIEM), and security operations and action response (SOAR).
As AI continues to evolve, cyber security solutions are constantly innovating to counter the unique threats that result.
Cloud Security - Protecting Cloud Environments
Cloud security is a tool designed to protect cloud infrastructure, applications, and data. Cloud security is not an independent part because it involves protecting networks, applications, and data in the cloud. Security responsibility depends on the deployment model. Cloud providers always manage physical security, while customers always manage edge security. The middle layer is usually the result of joint efforts with cloud providers, who provide native security tools in their products and assume that customers should take additional measures to protect their environment.
Cloud security vendors include hyperscale companies (AWS, Microsoft, GCP), security companies (Palo Alto, CrowdStrike), and cloud security companies (Wiz, Orca).
Software security - protecting software development and deployment
Security software development is becoming increasingly important. Most security bugs are introduced during the coding phase, but are not discovered until late testing or deployment. The later vulnerabilities are discovered, the higher the cost of fixing them. Therefore, people are paying more and more attention to security development, which has led to the emergence of the term DevSecOPs. It focuses on integrating security practices into software development, rather than applying security features at the end of the process.
Multiple vendors offer application protection, including hyperscale vendors, cloud security platforms, Synopsys, Snyk, Cloudflare, and others.
Data Security - Protecting Data
The core of cyber security is to protect data, so data security runs through the entire security lifecycle. The essence of security is prevention, detection, and response, so data security mainly revolves around these three aspects.
Infrastructure Security - Protecting Data centers and physical infrastructure
Part of cyber security is protecting physical infrastructure, such as IoT devices, data centers, etc. Common examples of hardware security include hardware firewalls or proxy servers, which scan incoming and outgoing traffic from physical networks for potential threats.
The importance of IoT security is also rapidly increasing, as it connects endpoint security, hardware security, and cloud security. Physical security also plays an important role in ensuring that unauthorized users cannot physically access machines/servers.
2. In the cyber security ecosystem, what are the positions and advantages of the giant companies?
Next, the RockFlow investment research team will conduct an in-depth analysis of the positions of global cyber security giants in their respective ecosystems. All of these companies offer cyber security ecosystem products and strive to provide customers with integrated security platforms. However, their main directions and advantages are different, so they have different investment values. Only by understanding their differences and competitive edges can we better understand their future.
Microsoft, one of the strongest cloud giants, offers a comprehensive portfolio of cyber security products
In January 2021, Microsoft's cyber security revenue exceeded $10 billion. Just two years later, Microsoft announced that its security revenue exceeded $20 billion.
Microsoft's cyber security product portfolio consists of six main parts: Defender, Sentinel, Entra, InTune, Priva, and Purview. Defender covers cloud, application, endpoint, IoT and other scenarios, and is Microsoft's cross-solution security product. Sentinel is a SIEM/SOAR solution. Entra is Microsoft's IAM solution. InTune is a unified endpoint management tool. Priva covers data privacy and compliance. Purview is a data governance tool.
Google, one of the strongest cloud giants, is committed to cyber security and data protection
One of Google's main goals is to become the first choice in the field of cloud security. They are excellent in building product portfolios, providing cyber security through load balancing, cloud firewalls, and secure network proxies. GCP provides multiple data protection services (built on its advantages as a data company). They also focus on protecting DevOps through various SecDevOps tools.
In 2022, Google acquired Mandiant for $5.40 billion, which enhanced GCP's managed service offering capabilities. Combined with its data governance, observability, and SIEM/SOAR solutions, GCP is expected to become a strong player in the security space.
Cisco, the old internet company, has become one of the largest security companies through mergers and acquisitions
Cisco has a series of highly competitive security products. After acquiring Splunk in 2023, Cisco became one of the largest security companies in the world. This is Cisco's largest acquisition in history and the largest acquisition in the IT industry in 2023. In the 2023 fiscal year, Cisco's security revenue was about $4 billion, while Splunk's ARR at the end of the same quarter was $3.70 billion.
Cisco's core security advantage comes from its vast network business. They also extend to cloud, endpoint, and SASE. Splunk brings strong SecOps influence through SIEM, SOAR, and analytics.
Palo Alto Networks, the world's largest pure cyber security company by revenue
Palo Alto is the highest-grossing pure cyber security company in the world. Its core product is network firewall (hardware and software); through an aggressive acquisition strategy, they have greatly expanded their product portfolio. Their goal is to become an integrator in the cyber security field and they are continuing to move towards this goal.
Palo Alto has four main solutions: Strata (networking), Prisma (cloud, access), Cortex (endpoint, SecOps), and Unit 42 (managed services). Last quarter, Palo Alto Networks' recovery was mainly due to its next-generation security (NGS) platform and AI products. This quarter, the company continued to maintain strong performance, and its latest developments highlight its leadership position in the cyber security field.
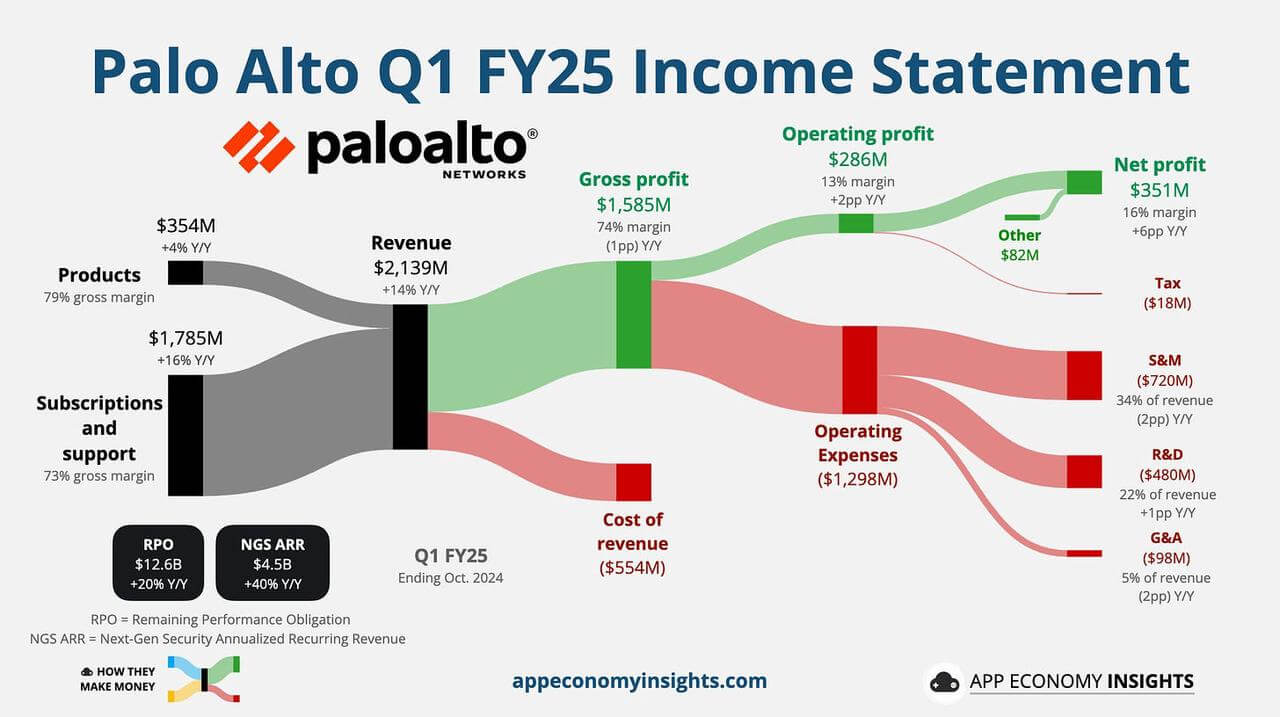
It is worth noting that in Palo Alto's disclosure, AI occupies a central position: AI integration continues to play a transformative role. Products such as AI Runtime Security and AI-SPM are gaining increasing attention, with over 750 AI applications protected and AI-driven features embedded in Palo Alto's SASE and Cortex platforms.
In addition, its NGS ARR continues to grow: the next generation security ARR increased by 40% year-on-year to $4.50 billion (slightly slower than the 43% in the fourth quarter of fiscal year 2024), driving the growth of subscription revenue. The company raised its full-year NGS ARR forecast to 32%.
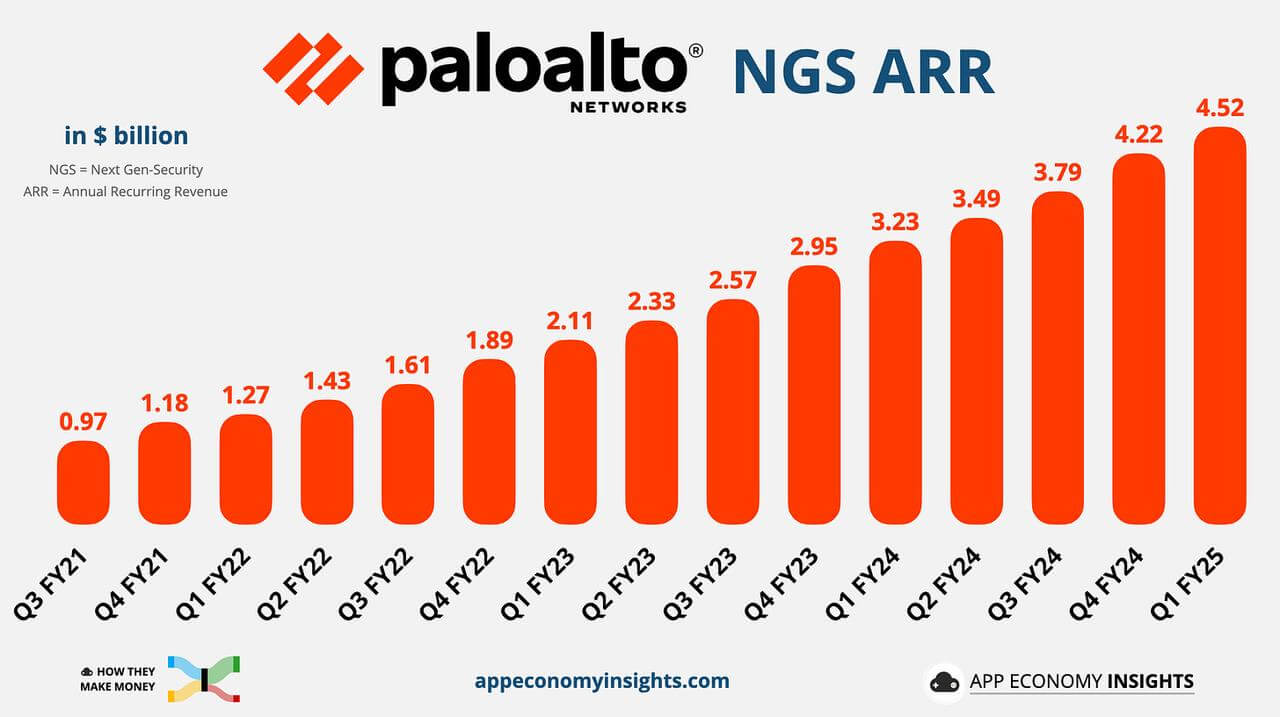
Overall, Palo Alto Networks has solidified its leading position in cyber security by combining platformization with AI innovation. With its strong NGS growth and expanding product portfolio, the company is on track to achieve its long-term goal of becoming the first cyber security company to achieve $15 billion in annual revenue.
Fortinet, the world's second highest-grossing pure cyber security company
Fortinet is the second highest-grossing pure cyber security company in the world. Like Palo Alto, their core product is firewall (hardware and software). Fortinet remains primarily a cyber security company (accounting for 60-70% of revenue) and focuses on providing powerful SASE products to achieve growth.
That being said, they have a broad portfolio of security products, including cloud security, application security, data security, and managed services. Fortinet's revenue in the past 12 months was $5.30 billion.
Crowdstrike, a key leader in end point security
Crowdstrike's core product is end point security. In terms of end point security, they are one of the two market leaders (the other being Microsoft). In terms of cloud and software security, they have a unified platform for situational management, workload protection, and application protection. They provide data protection suites and services for cross-security operations. They do not provide identity and access management, but they provide identity security for protecting other IAM products.
Zscaler, leader in cloud security with over 500 billion daily transactions
As a leader in cloud security, Zscaler's Zero Trust Exchange cloud security platform has more than 500 billion daily transactions, which is nearly 60 times the total daily Google searches. This milestone highlights the importance and industry position of Zscaler's platform. By extracting security signals from 500 billion daily transactions and using advanced AI models to analyze these signals in real time, Zscaler has the ability to fully understand the evolving threat landscape. This advancement provides customers with superior threat detection, prevention, and response capabilities.
Zscaler Zero Trust Exchange is the world's largest secure Cloud Computing Platform, providing comprehensive security protection for users, devices, workloads, and applications. Zscaler serves over 8,600 customers and over 47 million users. With a huge data foundation, it is expected to enhance the AI capabilities of the cyber security industry, not only enabling organizations to reduce risks and optimize performance, but also paving the way for AI-driven comprehensive zero-trust platforms.
Cloudflare's performance continues to grow rapidly, and the future path is still broad
Cloudflare provides information delivery network (CDN) services, which essentially help promote a faster and more secure internet. As one of the strong performers in the cyber security industry, the company has done an excellent job in maintaining a growth rate higher than the market through a product-led strategy. It offers a variety of cyber security and infrastructure products, and its security service product Cloudflare One is managed by a unified Console and offers free packages for up to 50 users.
RockFlow's investment research team believes that the company has a large and stable customer base and has the opportunity to expand through its Cloudflare One product. In addition, given Cloudflare's simple pricing model, adopting a tiered pricing method is also beneficial for future business growth.
In the latest quarter, the company's revenue grew 28% to $430 million, beating market expectations.
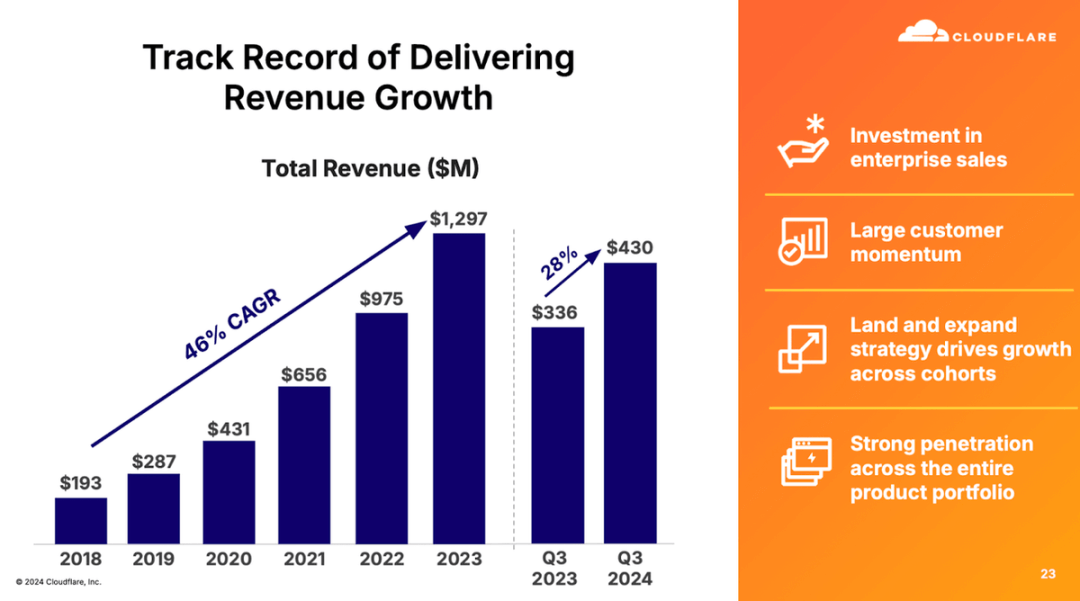
In addition, Cloudflare's revenue growth rate has remained stable in the past few quarters.
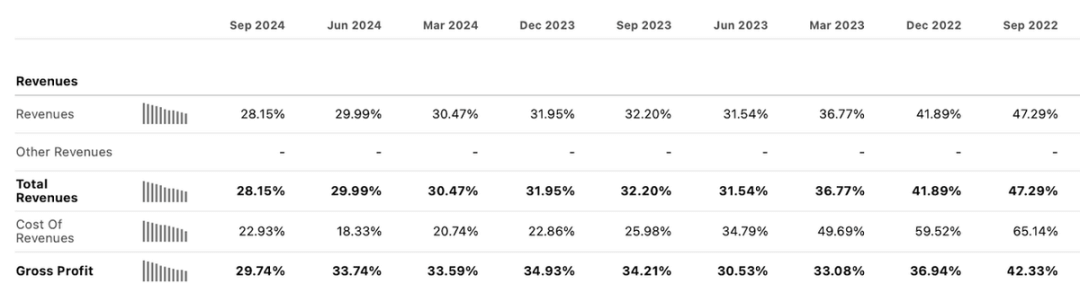
During the latest earnings call, management stated that "we have reached a turning point in rebuilding the marketing team." They believe that their sales efficiency continues to improve and "has returned to the best level of 2022."
3. Conclusion
The RockFlow research team believes that cyber security has a very optimistic development prospect. There are three main reasons why we are optimistic about the development of this industry in the long term: high demand, strong pricing power, and huge TAM (addressable market size).
However, given the extremely fierce competition and fragmentation in the industry, and the fact that tech giants have important distribution networks and product portfolios, we are most optimistic about the continued development of current giants and the top companies that have become vertical giants and have important differentiated platforms.
Author Profile:
The RockFlow research team has a long-term focus on high-quality companies in the US stock market, emerging markets such as Latin America and Southeast Asia, and high potential industries such as encryption and biotechnology. The core members of the team come from top technology companies and financial institutions such as Facebook, Baidu, ByteDance, Huawei, Goldman Sachs, CITIC Securities, etc. Most of them graduated from top universities such as Massachusetts Institute of Technology, University of California, Berkeley, Nanyang Technological Institute, Tsinghua University, and Fudan University.
Additionally, you can also find us on these platforms: